Password managers are secure and efficient tools designed to enhance digital security by simplifying and fortifying the management of passwords. Acting as a centralized repository, they store and encrypt users login credentials for various online accounts, such as websites, applications, and services. Users need to remember only one master password, granting them access to the password manager’s vault.
These tools typically offer features like password generation, secure storage, and the ability to auto-fill login details, reducing the need for users to memorize complex passwords. By prioritizing robust encryption techniques, password managers safeguard sensitive information from unauthorized access. Additionally, they often incorporate functionalities like multi-factor authentication and secure sharing, providing users with a comprehensive solution for maintaining strong, unique passwords across their digital footprint. With the rising importance of cybersecurity, password managers serve as a cornerstone for individuals and businesses seeking an effective and user-friendly way to protect their online identities.
How does a Password Manager Work
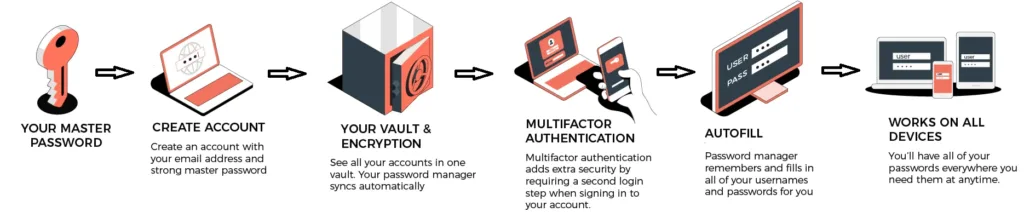
A Password manager works by providing a secure and centralized platform for users to store, organize, and retrieve their various login credentials. The process typically involves the following steps:
Creation of a Master Password: Users set up a master password, a single strong password that serves as the key to access their password manager. It’s crucial to choose a unique and memorable master password.
Secure Storage: Once logged in with the master password, the password manager securely stores all other login credentials in an encrypted vault. This vault can only be unlocked with the master password.
Password Generation: A Password manager often include a password generation feature. Users can create complex and unique passwords for each account, reducing the risk associated with using easily guessable or repeated passwords.
Auto-Fill and Auto-Login: When accessing a website or application, the password manager can automatically fill in the login details or facilitate a one-click login, eliminating the need for users to remember or manually enter passwords.
Encryption: Passwords stored in the manager’s vault are encrypted, meaning they are scrambled into unreadable text. This encryption adds an extra layer of security, ensuring that even if the vault is accessed, the stored passwords remain protected.
Multi-Factor Authentication (Optional): Some password managers offer multi-factor authentication options, adding an additional layer of security by requiring users to verify their identity through a second method, such as a code sent to their mobile device.
Cross-Device Synchronization: Many password managers offer synchronization across multiple devices. Changes made on one device, such as adding a new password, will reflect on all linked devices.
In summary, password managers streamline the process of managing and securing multiple passwords, promoting strong and unique credentials for each account while simplifying the user experience. They prioritize encryption, master password protection, and other security measures to safeguard sensitive information.
How does a password manager encrypt passwords?
Password managers use strong encryption algorithms to protect and secure passwords stored in their vaults. The primary encryption methods employed by password managers are:
AES Encryption (Advanced Encryption Standard)
AES is a widely used symmetric encryption algorithm. In the context of password managers, symmetric encryption means that the same key is used for both the encryption and decryption of data. The master password chosen by the user serves as the key for AES encryption. When a user logs in with the master password, the password manager uses it to decrypt the stored passwords for use. AES encryption is renowned for its security and efficiency.
Hashing and Salting
Password managers often use cryptographic hashing and salting techniques to enhance security. Hashing transforms the master password into a fixed-length string of characters, making it computationally infeasible to reverse the process and obtain the original password. Salting involves adding a unique random value (salt) to each password before hashing, preventing attackers from using precomputed tables (rainbow tables) for password cracking.
Key Derivation Functions (KDFs)
Password managers employ Key Derivation Functions to convert the master password into an encryption key. KDFs make brute-force attacks more challenging by slowing down the password derivation process. Popular KDFs include PBKDF2 (Password-Based Key Derivation Function 2) and Argon2.
Zero-Knowledge Architecture
Some advanced password managers adopt a zero-knowledge architecture, meaning that even the service provider cannot access or decipher user data. In this setup, encryption and decryption occur locally on the user’s device, with the master password never transmitted or stored on the provider’s servers.
End-to-End Encryption
In cases where the password manager offers synchronization across multiple devices, end-to-end encryption ensures that data is encrypted on the user’s device and only decrypted on other authorized devices. This prevents the service provider from accessing sensitive information.
By combining these encryption methods, password managers create a secure environment for storing and managing passwords, significantly reducing the risk of unauthorized access to sensitive user data.
Types of Password Managers
Password managers are categorized according to the features they offer. These include storage capability, size and location, level of encryption and special services offered, among others. Following are the commonly used types:
There are primarily three main types of password managers:
Local Password Managers
- Description: Local password managers store encrypted password data locally on the user’s device. They do not rely on cloud services for synchronization.
- Key Features:
- Data remains on the user’s device, reducing the risk of cloud-based attacks.
- Often lower subscription costs as they don’t require server infrastructure.
- Limited accessibility to passwords across multiple devices.
Cloud-Based Password Managers
Description: Cloud-based password managers store encrypted password data on remote servers, allowing users to access their passwords across multiple devices.
- Key Features:
- Synchronization across devices for seamless access.
- Enhanced security measures, such as multi-factor authentication (MFA).
- Convenient access to passwords from any device with an internet connection.
Offline Password Managers
- Description: Offline password managers operate without an internet connection, providing an extra layer of security by keeping all data stored locally.
- Key Features:
- No reliance on cloud services, reducing the risk of online attacks.
- Often preferred by users who prioritize privacy and want to minimize exposure to cloud vulnerabilities.
- Limited or no synchronization across multiple devices.
Each type of password manager has its own set of advantages and considerations. The choice between them depends on factors such as user preferences, security requirements, and the need for cross-device accessibility.
Pros & Cons of Password Managers
Pros of Password Managers
Enhanced Security:
- Pro: Password managers generate and store complex, unique passwords for each account, reducing the risk of using weak or repeated passwords.
Convenience:
- Pro: Users only need to remember one master password, streamlining access to multiple accounts.
Time-Saving:
- Pro: Password managers can auto-fill login credentials, saving time and effort during the login process.
Cross-Device Access:
- Pro: Cloud-based password managers offer synchronization across devices, allowing users to access passwords from anywhere.
Encrypted Storage:
- Pro: Passwords are stored in encrypted form, adding an extra layer of protection against unauthorized access.
Password Generation:
- Pro: Password managers can generate strong, random passwords, eliminating the need for users to create their own.
Cons of Password Managers:
Single Point of Failure:
- Con: The master password is a critical point of vulnerability; if forgotten or compromised, it can lead to unauthorized access.
Initial Setup:
- Con: Setting up a password manager and updating passwords can be time-consuming initially.
Dependency on Master Password:
- Con: If the master password is lost or forgotten, there may be limited options for recovery, and stored data may become inaccessible.
Cost:
- Con: Some advanced features or cloud-based services may come with a subscription cost.
Trust in the Provider:
- Con: Users must trust the security practices of the password manager provider, especially with cloud-based solutions.
Device Compatibility:
- Con: Compatibility issues may arise with certain devices or platforms, limiting the accessibility of passwords.
Balancing these pros and cons helps users make informed decisions about whether a password manager is the right solution for their needs.
Recommended Password Managers
Here is a list of recommended best password managers, along with key features that make them popular choices:
- LastPass:
- Key Features: Secure storage, password generator, multi-factor authentication, cross-device syncing, and a user-friendly interface.
- Dashlane:
- Key Features: Strong password generator, secure sharing of credentials, dark web monitoring, and a built-in VPN for additional security.
- 1Password:
- Key Features: Advanced encryption, travel mode for added security during international travel, secure document storage, and Watchtower for monitoring compromised passwords.
- Bitwarden:
- Key Features: Open-source and self-hosted options available, strong encryption, secure password sharing, and a free version with essential features.
- Keeper:
- Key Features: Biometric login, secure file storage, breach monitoring, and a private vault for sensitive documents.
- NordPass:
- Key Features: Developed by the team behind NordVPN, zero-knowledge architecture, secure sharing, and a straightforward interface.
- RoboForm:
- Key Features: Secure password sharing, application logins, emergency access feature, and identity management for filling forms.
- KeePass:
- Key Features: Open-source and free, local storage of passwords, strong encryption, and a large community for support and plugins.
- Enpass:
- Key Features: Local storage with the option to sync using various cloud services, strong encryption, and one-time purchase without subscription fees.
- RememBear:
- Key Features: User-friendly design, strong encryption, biometric login, and a fun approach to password management.
Are Password Managers Safe?
Password managers are completely safe if you use a trusted and popular password manager service. Whenever possible, it is always better to increase the security level of your passwords than to be complacent with the status quo, thinking you are safe as is. This is the function of password managers.
You might worry about the safety of your passwords stored in a password manager and the possibility of a hack. Can password managers be hacked?
Yes, if you are careless about leaving your password manager open on your desktop for a long time. Hackers can get “in” through your desktop or mobile, but as long as your password manager uses deep encryption, such as AES 256-bit, and is fully supported by multi-factor authentication or biometrics, you have nothing to worry about. Moreover, password managers do not keep a record of your master password.
Finally, when it comes to password managers, there is more to it than just solving the problem of remembering long and complicated passwords. Password managers provide an added layer of security for all your online accounts making it hard for crooks to crack them. Remember, the security of your passwords is only as good as how you want them to be.





