Shoulder surfing is a form of visual eavesdropping in which an individual observes, or “surfs,” the activities of another person, typically with the intent of gathering sensitive or confidential information. This technique involves someone looking over the shoulder of another person, often in crowded or public spaces, to gain unauthorized access to information such as passwords, PINs, or other confidential data.
The attacker, referred to as a “shoulder surfer,” takes advantage of the lack of privacy in certain situations, such as when a person is entering a PIN at an ATM, typing a password on a computer or mobile device, or filling out sensitive forms. The goal is to obtain information that can be used for malicious purposes, such as unauthorized access to accounts, identity theft, or other fraudulent activities.

To protect against shoulder surfing, individuals are advised to be vigilant in public spaces and take measures to shield their input devices or sensitive information from prying eyes. This may include using privacy screens on devices, covering the keypad when entering PINs, and being aware of their surroundings to detect and deter potential shoulder surfers. Additionally, organizations often promote awareness and provide guidelines to employees to minimize the risk of sensitive information being compromised through this method.
How does shoulder surfing happen?
Shoulder surfing typically occurs when an individual, known as a “shoulder surfer,” clandestinely observes another person’s activities, particularly when the target is entering sensitive information. Here’s how shoulder surfing can happen:
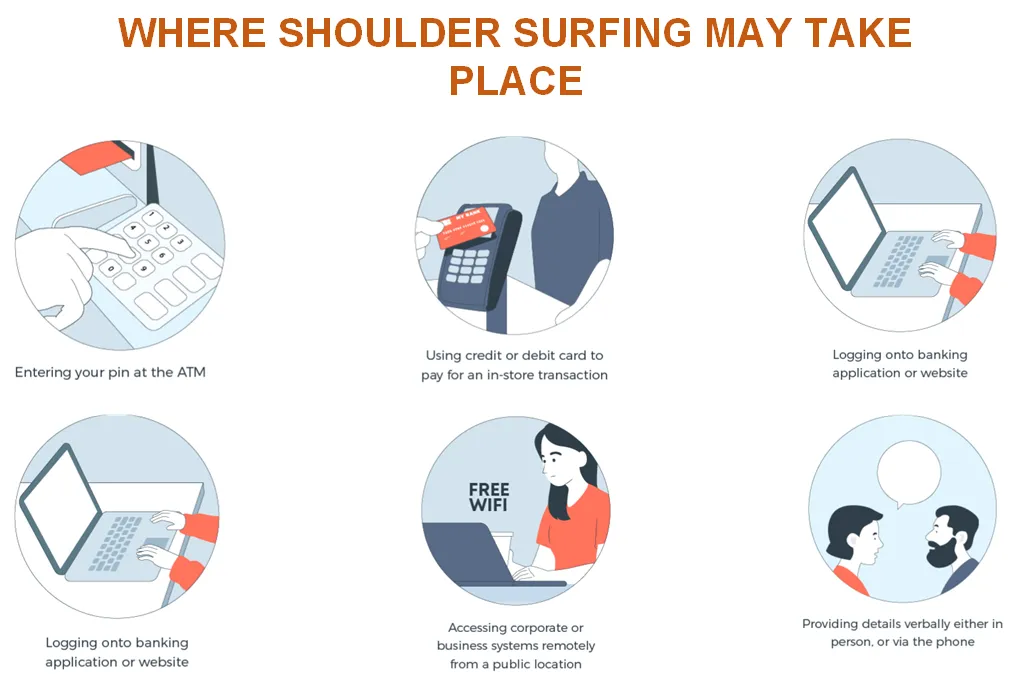
- Public Spaces: Shoulder surfing often takes place in crowded or public spaces where individuals are in close proximity to each other, such as public transportation, airports, cafes, or queues.
- ATM Transactions: One common scenario is at Automated Teller Machines (ATMs). A shoulder surfer may discreetly stand nearby and observe the PIN being entered when the user withdraws money or checks an account balance.
- Point-of-Sale (POS) Terminals: When individuals make purchases using debit or credit cards at point-of-sale terminals, a shoulder surfer may stand close by, attempting to glimpse the entered PIN.
- Mobile Device Usage: Shoulder surfing can happen when individuals use their smartphones or tablets in public places, especially when entering passwords, unlocking devices, or accessing sensitive apps.
- Computer Usage: In shared workspaces or public libraries, shoulder surfers may watch individuals typing passwords or entering login credentials on computers.
- Form-Filling: In situations where individuals are required to fill out forms containing sensitive information, such as in a doctor’s office or at a bank, a shoulder surfer may attempt to view the information being entered.
- Unsecured Wi-Fi Networks: In locations with unsecured Wi-Fi networks, a malicious actor could attempt to intercept or observe the data being transmitted, including sensitive login credentials.
What are the types of shoulder surfing?
- PIN Observation: Shoulder surfers may focus on observing individuals entering their Personal Identification Numbers (PINs) at ATMs, point-of-sale terminals, or when making electronic transactions. The objective is to gain unauthorized access to the associated accounts.
- Password Theft: In settings where individuals log in to computers, mobile devices, or online accounts, shoulder surfers may aim to capture passwords. This could happen in public spaces, shared work environments, or even within organizations if individuals are not mindful of their surroundings.
- Document Scanning: Shoulder surfers may scan documents, forms, or paperwork being filled out by individuals in public spaces. This could include sensitive information such as addresses, phone numbers, or financial details.
- Mobile Device Access: Observing the unlocking patterns, passwords, or PINs on mobile devices is a common type of shoulder surfing. This can occur in public transportation, waiting areas, or any place where people use their smartphones.
- Credential Theft in Crowded Places: In crowded places like concerts, festivals, or sports events, shoulder surfers may take advantage of the close proximity to capture usernames, passwords, or other credentials as individuals access their accounts on mobile apps.
- Form Entry: Shoulder surfers might target individuals filling out forms that contain personal or sensitive information. This could include medical forms, application forms, or any document that requires the input of confidential details.
- Login Credential Capture: In shared workspaces or areas with communal computers, shoulder surfers may attempt to capture login credentials as individuals enter them to access their workstations or online accounts.
- Wi-Fi Network Eavesdropping: In scenarios where individuals connect to public Wi-Fi networks, shoulder surfers may try to observe the information being entered during the login process, including usernames and passwords.
consequences for shoulder surfing crimes
Shoulder surfing itself is generally not considered a distinct criminal offense, but rather a method employed by individuals with malicious intent to gather sensitive information. The consequences for activities resulting from shoulder surfing can vary depending on the nature of the information obtained and the actions taken by the perpetrator. Here are potential consequences:
- Identity Theft: If a shoulder surfer gains access to personal information such as names, addresses, social security numbers, or other identifiers, they may engage in identity theft. This can lead to financial fraud, opening accounts in the victim’s name, or other criminal activities.
- Financial Loss: Shoulder surfers targeting PINs or passwords may use the obtained information to access bank accounts, credit cards, or other financial accounts, resulting in financial losses for the victim.
- Unauthorized Access: Shoulder surfers capturing login credentials for email accounts, social media, or other online platforms may gain unauthorized access to the victim’s digital presence. This could lead to privacy breaches, spreading false information, or even cyberbullying.
- Fraudulent Transactions: Shoulder surfers obtaining credit card information may engage in fraudulent transactions, making purchases or withdrawals without the victim’s consent.
- Sensitive Information Exposure: Individuals filling out forms in public spaces may unknowingly expose sensitive information. This can lead to privacy violations and potential misuse of the disclosed details.
- Legal Consequences: Depending on the severity of the actions taken by the perpetrator after obtaining information through shoulder surfing, they may face legal consequences such as charges related to identity theft, fraud, or unauthorized access to computer systems.
Mitigating the Risks of Shoulder Surfing
Mitigating the risk of shoulder surfing involves cultivating a heightened sense of awareness and adopting protective measures. Individuals should be mindful of their surroundings, especially in public spaces, and take care to shield their PINs, passwords, or sensitive information when entering it on devices. Utilizing privacy screens on mobile devices can help prevent unauthorized viewing. Employers should promote cybersecurity awareness among employees, emphasizing the importance of securing information in shared workspaces. Implementing physical barriers or rearranging workstations to reduce visibility can further deter shoulder surfing. Additionally, fostering a culture of vigilance and education within organizations can contribute to a collective effort in minimizing the risk of this subtle yet potentially damaging form of information theft.
Conclusion
To mitigate the risk of shoulder surfing and its consequences, individuals are advised to practice awareness in public spaces, shield their input devices when entering sensitive information, and adopt secure behaviors such as using privacy screens on mobile devices. Organizations also play a role in promoting cybersecurity awareness and implementing measures to protect individuals from the potential fallout of shoulder surfing activities.





