DLL hijacking is a devastating attack method that takes advantage of how Dynamic Link Libraries (DLLs) are handled in Windows. It consists of creating a malicious version of a legitimate DLL required by the program and placing it early in the search order used to find a required DLL. This folder is commonly the same folder as the executable. When the executable is launched, it will find the malicious version with the same name in the same folder, loading that instead and infecting the computer.
Clearly, if applications that are automatically loaded upon startup are compromised with a tainted DLL file, cybercriminals will be granted access to the infected computer whenever it loads. At this point in time, only Microsoft operating systems are susceptible to DLL hijacks. DLL hijacking is not a new form of cyber-attack. Its first appearance can be traced back to the launch of Windows 2000.
How Does DLL Hijacking Work?
For a DLL hijacking attack to be successful, a Windows application needs to be tricked into loading an infected DLL file instead of the legitimate DLL. The flow diagram of this attack is shown if below.
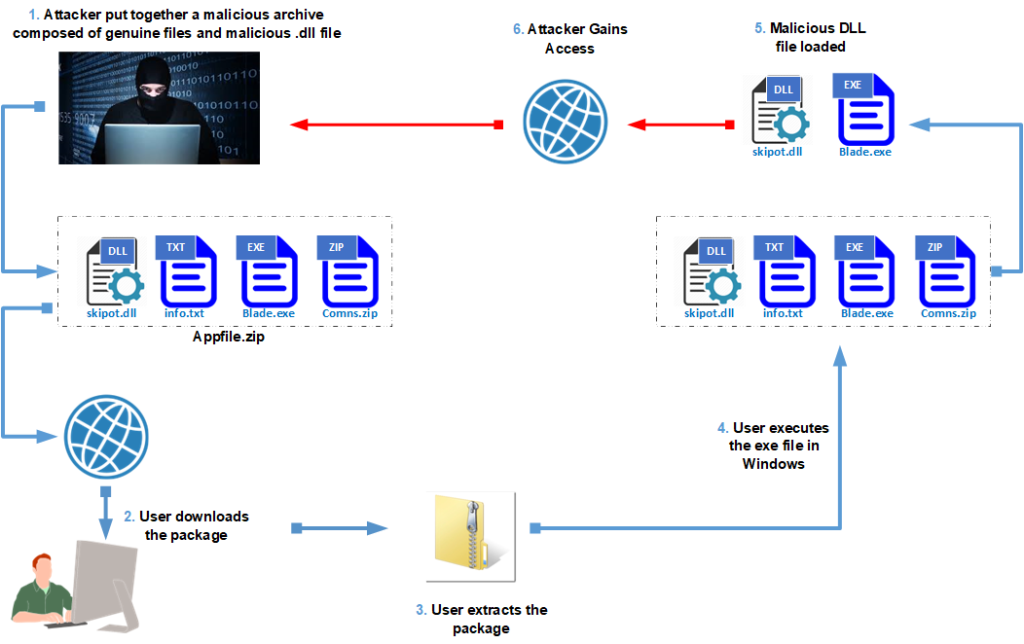
Successful Attacks using DLL injection
1. U.S Government cyber attack
The recent cyber-attack against the US Government is possibly the largest breach in the US security industry.
How it Happened
In March 2020, a malicious code was injected into the U.S government’s internal systems through an IT update from its network-monitoring vendor, SolarWinds using a DLL injection attack. The cybercriminals used a supply chain method of attack, where malicious code (malicious DLL) is introduced into a system through a compromised third-party.
The cyber attackers accessed the Microsoft Office 365 account of the National Telecommunications and Information Administration (NTIA), uncovering a swathe of internal communications between several federal agencies.
Affected Entities
It has been discovered that six (6) U.S Government departments have been breached, including:
- The Department of Energy
- The National Nuclear Security Administration
- The U.S Department of State
- The U.S Department of Commerce
- The U.S Department of the Treasury
- The Department of Homeland Security
What is speculated?
Mounting evidence suggests that Russia was responsible for the attack, though the nation explicitly denies any involvement.
Andrei Soldatov told the Guardian that the hack was most likely a joint effort between Russia’s foreign intelligence outfit SVR (the successor to the KGB), and FSB, the domestic spy agency Putin led before he became Prime Minister and President.
The cyber attackers were very specific with the intelligence they penetrated. Investigations are slowly uncovering and mapping the digital tracks of the threat actors to discover the specific sectors they were targeting.
Microsoft President Brad Smith said that 80% of the affected victims are located in the United States, with the remaining 20% spread across, Spain, Israel, United Kingdom, Belgium, and the United Arab Emirates.
2. Qbot Attack Affects 2 Major Corporations
The notorious banking trojan Qbot has been in business for more than a decade. The malware, which has also been dubbed Qakbot and Pinkslipbot, was discovered in 2008 and is known for collecting browsing data and stealing banking credentials and other financial information from victims.
It is highly structured, multi-layered, and is being continuously developed with new features to extend its capabilities. These new ‘tricks’ mean that despite its age, Qbot is still a dangerous and persistent threat to organizations. It has become the malware equivalent of a Swiss Army knife.
Recently, two major corporations were hit by this malware namely:
JBS
- Headquartered in Brazil
- Largest meat producer in the world
- Attacked via U.S. and Australian IT systems
- This attack occurred in the early morning of May 31, 2021
- “The company took immediate action, suspending all affected systems, notifying authorities and activating the company’s global network of IT professionals and third – party experts to resolve the situation.” – A statement from JBS USA
- Led to shutdown of multiple food production sites due to loss of network access
- Attack halted cattle slaughtering at all its U.S. plants for a day
- Extended shutdown could significantly disrupt food supply chains
- JBS claimed attack did not affect backups, but BleepingComputer reported that there were two encrypted/corrupted datasets that had prevented the company from going back online immediately
- Resulted in $11 million ransom payment
- JBS claims that “preliminary probe results show no company, customer or employee data was compromised in the attack”
- Forensic investigation ongoing
FUJIFILM
- Headquartered in Japan
- A major provider of medical imaging capabilities, although there were no reports that these were compromised
- The first signs of Qbot infection appeared on May 15, 2021, according to CEO of Advanced Intel, Vitali Kremez
- In the late evening of June 1, 2021 (JPT), FUJIFILM became aware of the possibility of a ransomware attack. As a result, the company took measures to suspend all affected stems in coordination with various global entities.
- “FUJIFILM Corporation is currently carrying out an investigation into possible unauthorized access to its server from outside of the company. As part of this investigation, the network is partially shut down and disconnected from external correspondence.”
- On June 1, 2021, FUJIFILM USA added an alert to the top of their website stating that they are experiencing network problems that are affecting their phone and email systems.
- The company was forced to take down portions of its network worldwide
- At approximately 10:00 AM EST on June 1, FUJIFILM told employees to shut off their computers and all servers immediately, including access to email, the billing system, and a reporting system.
- Claimed to have restored normal operations by June 14
- FUJIFILM stated that the “investigations completed so far have found no evidence of information leakage to the outside world.”
- No ransomware site has posted FUJIFILM data as of this publication
3. How to Protect Against DLL Injection?
There are a couple of ways by which we can secure ourselves from DLL Hijacking whether it is from developer or the user’s perspective. Let us discuss some best practices:
Secure Coding best practices: Developers have to use secure coding best practices where they can specify the location of all the associated DLL files so that there is no need to look for the DLL anywhere other than the program’s folder.
Use antivirus: Nowadays, antivirus software is so sophisticated that it can detect malicious attempts and prevent them from being executed, preventing malicious DLL files from replacing legitimate DLL files. Consequently, it is critical to maintain antivirus software up to date in order for it to detect malicious DLL attempts and take appropriate action against them.
User Awareness Training: DLL Injection attacks and threat groups behind it keep evolving their techniques throughout the years. As it is typically delivered via phishing emails, the most effective way to protect against this malware is with Advanced Threat Protection for email. VirtualDoers SaaS Defense helps protect against phishing and multiple types of malwares. Its data-independent technology scans email attachments, links, and content to detect unknown threats at first encounter before they reach the end-user.
Security infrastructure Improvement: Organizations must strengthen their security policies in order to tighten security, which is achieved with the help of continuous monitoring and the identification of the attack surface. Because a smaller attack surface exists within an organization, it will be beneficial to the organization.
4. Conclusion
DLL hijacking is a serious attack since it allows an attacker to execute malicious files on a Windows machine, causing significant damage to the business. As a result, precautions must be taken to avoid this type of attack. We have presented a handful of mitigation approaches or techniques. There could be more depending on the needs of the business, but these are some of the most effective ones. As a result, anytime an organization receives files or resources from outside the organization, the data or resources must be thoroughly examined.





