A shoulder Surfing Attack is a social engineering technique where an attacker simply looks over someone’s shoulder to get confidential information. It could be as simple as when a person is entering their PIN in an ATM or when a person is entering the username and password to their social media account/Internet Banking etc. A shoulder surfer could just be a person or sometimes it could be sophisticated video cameras, binoculars, CCTV, and Spy cameras to spy over the victim and steal their confidential information. If we look at the phases of hacking, Social Engineering is one of them. Social engineering is the art of exploiting humans to steal confidential information. Social engineering attacks can be grouped into three types:
- Human-based
- Mobile-based
- Computer-based
Shoulder surfing attack falls under the first type, human-based exploitation.
Why is Shoulder Surfing Used?
“No cost,” “no required skills,” “no tracking possible” and “no use of tools” are some of the usual reasons of using shoulder surfing by attacker.
Apart from all the illegal benefits, shoulder surfing attack is also done ethically to evaluate a corporate organization’s security posture usually during a Red Team engagement. Shoulder surfing attacks in cybersecurity are carried out by Security professionals or Ethical Hackers who have some of the best Ethical Hacking Certifications obtained using some of the best online Security courses available. Usually, these are external consultants hired to evaluate an organization’s security posture. These consultants usually are disguised as plumbers, facility staff, or IT support staff and engage in many Social Engineering attacks where one of the first ones including a Shoulder surfing attack.
This engagement involving shoulder surfing in cyber security is done with all the required permissions and the NDA signed and it is done within the legal boundaries for evaluation and sometimes even to comply with many of the Corporate Compliance and Regulations requirements. This gives us a fair idea of the uses of shoulder surfing on the positive side, on how it is used to evaluate the security posture and cybersecurity awareness of its employees.
Well, as mentioned in this article, shoulder surfing is used to gain illegal access to systems, accounts etc., as well as to execute identity theft and steal confidential data. It is replicated exactly in the same way a hacker or hacking group does it in a controlled manner to evaluate the security controls in place to protect the data of an organization. The certifications mentioned here will teach you exactly that, to execute techniques and attacks in a controlled manner to evaluate the existing defensive controls and how to improve them.”
Examples of Shoulder Surfing Attack
- In a crowded train or bus where the device screen is visible to others, and phone conversations are audible easily. Many a time, this is the most common place where shoulder surfing is exploited.
- Spending money at a POS in a supermarket while the person right behind can take note of the PIN entered.
- The most common risk is when people connect to unsecured Wi-Fi networks in airports, hotels, etc, to exchange confidential information.
- The use of drones and CCTV can also be a major threat for enabling a shoulder surfing attack, this is precisely why we have no-fly zones in many areas which hold confidential information such as military bases, secret financial institutions, government offices, and historical heritage sites.
- While using your mobile phone to pay bills or enter an OTP in public places. Most commonly when people recite their credit card number while typing it.
- Shoulder surfing attack is also done by insider attackers.
How to Prevent Shoulder Surfing Attack
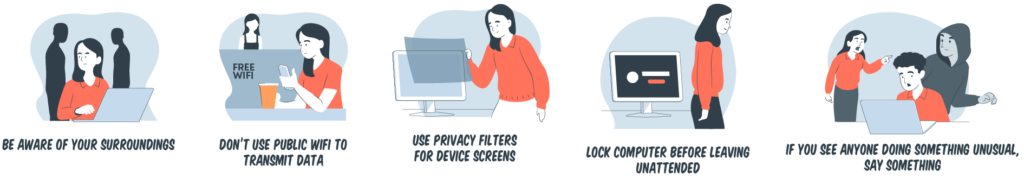
As mentioned, there are so many reasons to be worried about shoulder surfing. Here are some steps for shoulder surfing prevention and protection against shoulder surfing attacks.
Sit out of view: When working remotely in a public place, such as a coffee shop, make it a point to find a seat against a wall to keep away all those wandering eyes in front of you. Make sure the wall isn’t mirrored or all glass. If you’re sitting outside, try to avoid the crowd and set against a solid wall.
Maintain awareness of your surroundings: Watch for people, recording devices and other unwanted movements. Visual hacking is simple, quick and goes unnoticed so be very vigilant of your surroundings.
Use password manager: A password manager helps you store, manage and use your passwords securely. You don’t have to enter your password whenever you want to access something. The password manager will do it for you. Since there is no password to enter, there is no password to steal.
Protect your PINs: Create a PIN that’s hard guess. Memorize it and keep it secret. Always shield your PIN when using an ATM by using your freehand, a purse or magazine to cover the keypad. Watch for people lurking while you’re at the ATM.
Avoid using public networks: Free public Wi-Fi systems are usually poorly configured and are prone to hacking and other cyber attacks. They are also often unencrypted, making it easy for criminals to hack them. If you must use a public Wi-F-, we recommend that you use a virtual private network or VPN. Better yet, stay at home and work from there.
Set strong passwords: Create strong passwords that can’t be cracked by brute force, dictionary attack or phishing. The best passwords are long and contain a good mix of letters, numbers and symbols, yet easy to remember. Avoid common substitutions and memorable keyboard paths like “qwerty”. Avoid reusing passwords that can lead to the compromise of one being the compromise of all.
Use biometric authentication: Biometric authentication is the strongest physical security technique that’s used for identification and authentication. It is hard to replicate because every retina, fingerprint and any other facial recognition feature is unique. So that even shoulder surfers steal your information, they will not be able to pass the biometric test.
Use two-factor authentication: Two-factor authentication is a security mechanism in which individuals provide two authentication factors to be able to access their accounts. The second factor may be a one-time password (OTP) or personal identification number (PIN). For more protection, you can also add another layer of security, such as biometrics or answering a security question.
Use contactless payment methods: A contactless payment method refers to a secure way of paying for products and services using a debit, credit, smartcard or other payment devices that applies radio frequency identification (RFID) and near-field communication (NFC). As its name suggests, there is no contact between the payment mode and the point of sale (POS) terminal. The payment takes effect when the mode of payment (debit card) is tapped near the POS.
Monitor your credit regularly: Monitor your credit regularly to get ahead of shoulder surfing. If there are transactions you don’t recognize in your credit account, immediately report the matter to the credit bureaus, particularly Experian, TransUnion or Equifax.
Conclusion
This article discusses Shoulder Surfing Attack and its effects as well as its preventive measures. Shoulder surfing is one of the easiest and most useful techniques used in Social Engineering to steal confidential information. Social Engineering is part of the hacking process regardless of whether it is ethical or not. One can join an ethical hacking online training program to excel in this field and enhance knowledge and growth in their career.





