Callback phishing is a specialized type of cyber-security email threat. In a Callback phishing attack, cyber-criminals attempt to impersonate a business through an email or a phone call to a target recipient claiming that a transaction initiated by the recipient has been successfully completed. The recipient is then advised to call on the provided phone number should she/he not in agreement with the amount charged.
Clearly, the provided telephone number will not be that of the business being impersonated but rather a fictional customer support line setup by phishing actors. The aim being to attempt to lure the recipient to submit confidential information. Callback phishing attacks aim to collect specific, sensitive information from the recipient; this includes credit card numbers and bank account information.
VirtualDoers Cyber Security Team has observed callback phishing attacks that impersonate PayPal, McAfee, CrowdStrike, etc. However, any organization could be impersonated in this type of attack. Callback phishing attacks are on the rise and have grown more than 600% in Q1 of 2021
An example of Callback phishing Attack
Below is an example of callback phishing attacks:
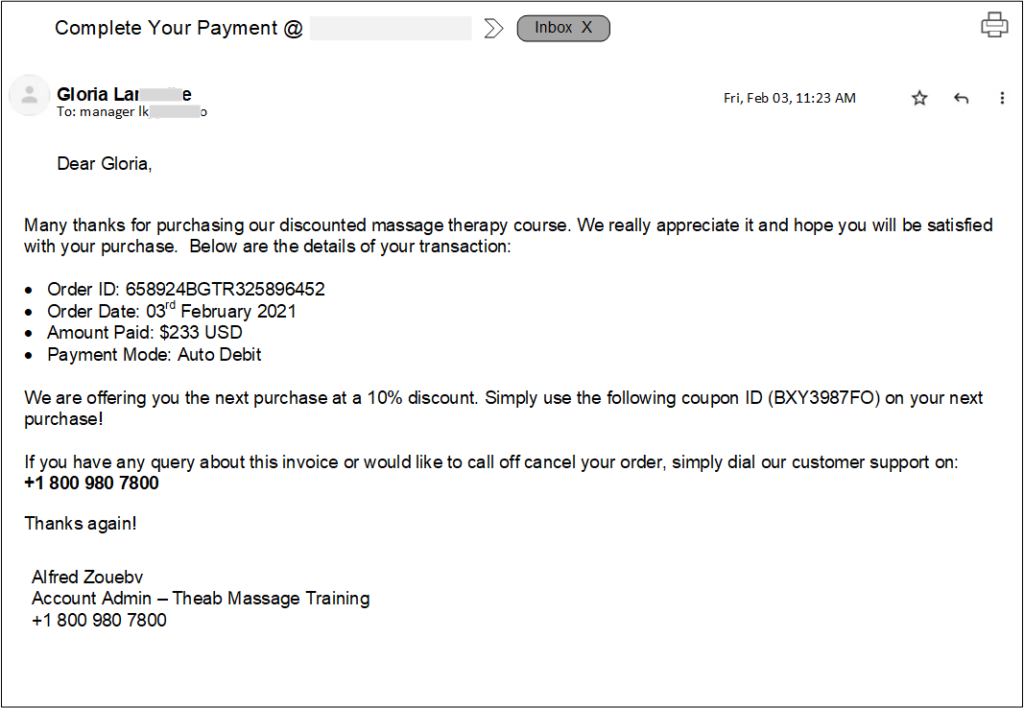
As mentioned earlier, perpetrators of the callback phishing attack attempt to lure the recipient of the message to give them a call to resolve the presented problem by tricking the victim into disclosing sensitive information.
We have also seen situations where those cybercriminals are allowed access into their target’s computers through remote desktop, and this allows those threat actors to install further backdoors or spread to other machines.
Callback phishing attacks were first introduced by the ‘BazarCall/BazaCall’ campaigns that appeared in March 2021 to gain initial access to corporate networks for ransomware attacks.
Callback phishing attacks were so successful that multiple ransomware and extortion gangs, such as Quantum, Zeon, and Silent Ransom Group adopted the technique to gain initial network access through unsuspecting employees. This type of threat also contributed to 24.6% of the overall share of Response-Based threats,” details the Agari report.
How to Detect Callback Phishing Attacks
Callback phishing attacks are unique in the sense that they easily bypass email filters. This is because they do not include malicious links or suspicious attachments. For that reason, email filters typically won’t catch them, so it’s important for organization to train their employees to be able to spot such threats.
The following tips will help you spot callback phishing attacks:
- scrutinize the sender: Ensure that the email is from the company it is purporting to be. Even email addresses can be spoofed, so this is not foolproof, but it is a great first step in the investigation process.
- Act like a Detective: Ask yourself, what does this email want me to do? If the language in the email is trying to convince you to do something (especially if it insinuates urgency), that is a red flag! In the examples above, the attacker is attempting to convince the mail recipient to ‘callback’. In some cases, attackers may try to convince you to click a fraudulent link. Be diligent before clicking any links within emails and do not call phone numbers that you can’t identify.
- Trust your Instinct: If you are skeptical, ask for help. After the initial investigation, you are still not sure, contact your IT team to do some further digging. Remember, causing a false alarm is much better than setting off a real one!
Preventing callback phishing attacks
Preventing callback phishing attacks involves a combination of awareness, vigilance, and implementing security measures. Here are some key steps to help prevent callback phishing:
- Employee Training and Awareness:
- Train employees to be cautious when receiving unsolicited phone calls, especially those requesting sensitive information.
- Educate them about the tactics used in vishing attacks, such as impersonation, urgency, and creating a sense of fear or panic.
- Verify Caller Identity:
- Before providing any information, verify the identity of the caller by asking for their name, organization, and contact details.
- Use official contact numbers obtained from legitimate sources to call back and confirm the authenticity of the request.
- Use Two-Factor Authentication (2FA):
- Implement two-factor authentication wherever possible. Even if attackers manage to obtain passwords, they would still need a second form of authentication to access accounts.
- Establish Communication Policies:
- Clearly define and communicate policies regarding the sharing of sensitive information over the phone.
- Encourage employees to verify the legitimacy of unexpected calls by contacting the requesting party through official channels.
- Limit Information Disclosure:
- Instruct employees not to disclose sensitive information, such as passwords, PINs, or financial details, over the phone, especially if the call is unexpected.
- Monitor and Report Suspicious Calls:
- Establish a reporting mechanism for employees to report suspicious calls. Encourage them to report any unusual requests for information.
- Monitor and analyze call patterns for any anomalies that might indicate a phishing attempt.
- Implement Call Filtering and Blocking:
- Use call filtering and blocking solutions to identify and block known malicious or suspicious phone numbers.
- Regularly update these solutions to stay ahead of emerging vishing threats.
- Regular Security Awareness Training:
- Conduct regular security awareness training sessions to keep employees informed about evolving phishing techniques, including callback phishing.
- Simulate vishing attacks during training to help employees recognize and respond appropriately.
- Implement Call Back Verification:
- If an employee receives a suspicious call requesting sensitive information, establish a protocol for them to call back using a known and verified contact number.
- Regularly Update Security Policies:
- Continuously review and update security policies to adapt to emerging threats. Ensure that employees are aware of any changes in policies related to phone-based attacks.
- Use Call Authentication Technologies:
- Explore the use of call authentication technologies, such as STIR/SHAKEN (Secure Telephone Identity Revisited/Signature-based Handling of Asserted information using toKENs), to verify the authenticity of calls.
Conclusion
One of the most important facets of effective cybersecurity awareness training is educating users beforehand on how they will or will not be contacted, and what information or actions they may be asked to take. “It is critical that users understand how they may be contacted by legitimate internal or external departments, and this goes beyond just cybersecurity.” Virtualdoers Technology team is here to help. If you have questions about ‘callback phishing’ attacks or want to discuss how we can help protect your business with cyber security services, contact us today.





