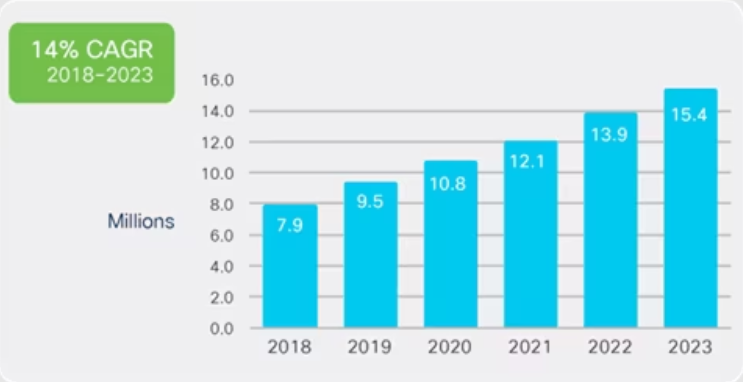
One of the first and notorious DDoS (Distributed Denial of Service) attack occurred in 1996 when Panix, now one of the oldest internet service providers, was knocked offline for several days by a SYN flood, a technique that has become a classic DDoS attack. Over the next few years, DDoS attacks will become common and Cisco predicts that the total number of DDoS attacks will double from the 7.9 million seen in 2018 to something over 15 million by 2023.
In the vast landscape of cyberspace, tales of digital battles echo through time. Today, we embark on a riveting journey through the annals of DDoS attacks—stories of chaos, resilience, and the invaluable lessons they’ve bestowed upon us. So, buckle up as we unravel the chronicles of notorious DDoS attacks and the wisdom we’ve gained from facing the storm.
Notorious DDoS Attacks Unveiled
DDoS attacks are like the tempests of the digital world—disruptive, powerful, and orchestrated with a touch of malicious brilliance. Instead of swords and shields, cyber assailants wield botnets, armies of compromised devices, to flood a target with an overwhelming volume of traffic. The goal? Overwhelm the defenses, rendering the online fortress defenseless.
1. The Great Dyn Attack: Internet’s Quake (2016)
In the autumn of 2016, a seismic event rocked the digital landscape. The Dyn attack, a massive DDoS assault, targeted the infrastructure of Dyn, a prominent Domain Name System (DNS) provider. The impact was swift and widespread, causing major websites and services, including Twitter, Reddit, and Netflix, to experience outages.
Lesson Learned: The Power of Targeting Critical Infrastructure
The Dyn attack underscored the vulnerability of foundational internet services. Cyber adversaries, by targeting key infrastructure, could bring down not just individual websites but disrupt the very fabric of the internet. The lesson was clear—strengthening the resilience of core internet components is paramount.
2. The Mirai Botnet: Unleashing the Digital Hordes (2016)
In the same year, the Mirai botnet emerged as a formidable force. What made Mirai unique was its ability to recruit and weaponize Internet of Things (IoT) devices, transforming them into foot soldiers for DDoS attacks. The targets ranged from gaming servers to internet service providers.
Lesson Learned: The Internet of Vulnerabilities
Mirai brought attention to the often-overlooked security vulnerabilities in IoT devices. From smart cameras to thermostats, these devices became unwitting accomplices. The lesson was clear—securing the expanding network of IoT devices is critical to preventing them from becoming tools of digital warfare.
3. GitHub’s 1.35 Tbps DDoS: A Gigantic Onslaught (2018)
In 2018, GitHub, a widely-used platform for software development, faced a colossal DDoS attack that reached an unprecedented scale—1.35 terabits per second. This overwhelming assault showcased the evolving capabilities of DDoS techniques.
Lesson Learned: The Arms Race in Cybersecurity
GitHub’s experience highlighted the need for continuous innovation in cybersecurity. As attackers refine their methods, defenders must stay ahead in the arms race. The lesson was clear—investing in cutting-edge cybersecurity measures is not a choice but a necessity.
4. The Memcached Reflection: Amplifying the Impact (2018)
In the same year, a new technique emerged—Memcached reflection attacks. Exploiting unsecured Memcached servers, attackers could amplify the volume of DDoS traffic, reaching up to 50,000 times the original request.
Lesson Learned: Unintended Consequences of Technology
The Memcached reflection attacks shed light on the unintended consequences of powerful technologies. Services designed to enhance performance, when left unsecured, could unwittingly become weapons. The lesson was clear—technological advancements must be accompanied by robust security measures.
5. The Cloudflare Flare-On: A Resilient Stand (2020)
In 2020, Cloudflare, a major internet security company, faced a relentless DDoS attack that peaked at 17.2 million requests per second. What made this incident notable was Cloudflare’s resilience, absorbing the colossal traffic without succumbing to the onslaught.
Lesson Learned: The Importance of Proactive Defense Strategies
Cloudflare’s successful defense highlighted the importance of proactive defense strategies. By distributing traffic across a global network and leveraging advanced security measures, they showcased the power of resilience in the face of adversity.
6. The Rise of Ransom DDoS (RDDoS): Pay or Perish (Ongoing)
In recent times, a disturbing trend has emerged—Ransom DDoS attacks. Cybercriminals, leveraging the threat of sustained DDoS assaults, demand ransom payments from organizations to prevent the attacks.
Lesson Learned: DDoS as a Business Threat
The rise of Ransom DDoS underscores the transformation of DDoS attacks into a business threat. Organizations must not only defend against disruptions but also navigate the delicate dance of extortion attempts. The lesson is clear—cybersecurity strategies must encompass both technical defenses and robust incident response plans.
Learn about other types of cyber attacks including phishing and ransomware and how to protect against them
Conclusion: Navigating the Digital Seas
As we navigate the digital seas, the tales of notorious DDoS attacks serve as beacons, illuminating the path forward. The lessons learned are not mere footnotes in cybersecurity history but guiding principles for the ongoing battle against digital tempests. Strengthening critical infrastructure, securing the IoT landscape, staying ahead in the cybersecurity arms race, understanding the unintended consequences of technology, and embracing proactive defense strategies—all are essential elements in our quest for a resilient and secure digital realm.
In the grand tapestry of cyberspace, the chronicles of DDoS attacks remind us that, while storms may rage, the human spirit of innovation, adaptability, and resilience prevails. So, fellow digital explorers, let these tales inspire us to fortify our defenses, learn from the past, and continue charting a course towards a safer and more secure digital future. Onward, into the digital horizon!





