A denial of service (DoS) attack is a type of cyber attack in which a malicious actor aims to render a computer or other device unavailable to its intended users by interrupting the device’s normal functioning. DoS attacks typically function by overwhelming or flooding a targeted machine with requests until normal traffic is unable to be processed, resulting in DoS to addition users. A DoS attack is characterized by using a single computer to launch the attack.
Denial of Services Real World Analogy
Imagine you’re throwing a small gathering at your house. Now, picture that instead of having a cozy get-together, you’re bombarded with a massive crowd, way more than your place can handle. People are pushing, shouting, and chaos ensues. This overwhelming situation prevents you and your guests from enjoying the party or even moving around comfortably. In the digital world, a similar scenario happens with what we call a DoS or, on a larger scale, a “Distributed Denial of Service” (DDoS) attack.
Usually when we talk about DDoS attacks, the resource being denied is a website and the “massive crowd” was maliciously caused by a hacker. But the concept is the same as a massive crowd at your gathering. Let’s dive into what DDoS means, the types of DDoS attacks, and methods of DDoS prevention.
What is a DDoS Attack? A Simple Definition
Since we’re all about making technical topics simple, let’s start with a basic answer to the question: What does DDoS mean ?
As mentioned above, a DDoS attack is a bit like a massive crowd on a website (but it’s intentionally caused by a hacker).
Here’s a simple definition for the meaning of DDoS:
A DDoS attack is when a hacker makes a website or other service inaccessible by flooding it with requests from many different devices.
DDoS Attack: The Cyber Traffic Tsunami
Now, imagine not just one person causing chaos but a whole army of troublemakers. That’s what happens in a DDoS attack. Instead of coming from one source, the attack is distributed, meaning it comes from many different devices all at once. These devices are often innocent computers or smart gadgets that have been taken over by the attacker without the owner knowing—a bit like an army of digital zombies.
If you’ve also heard the term “DoS attack,” don’t let that confuse you. A DDoS attack is just a specific type of DoS attack — one that uses multiple computers/devices to attack with.
How Does a DDoS Attack Work?
Just like a massive crowd floods a party with more people than it can handle, a DDoS attack floods a website with more requests (i.e. visitors) than the web server or other related systems can handle.
A DoS attack is like someone intentionally clogging the entrance to your online space. It could be a website, an app, or any online service. The attacker overwhelms it with more requests or traffic than it can handle. It’s akin to flooding your mailbox with thousands of letters so that the mail carrier can’t deliver your actual important mail.
Many hackers use botnets (a.k.a. zombie computers) to execute DDoS attacks. A botnet is a technique that allows a single person (hacker) to control thousands of devices at once.
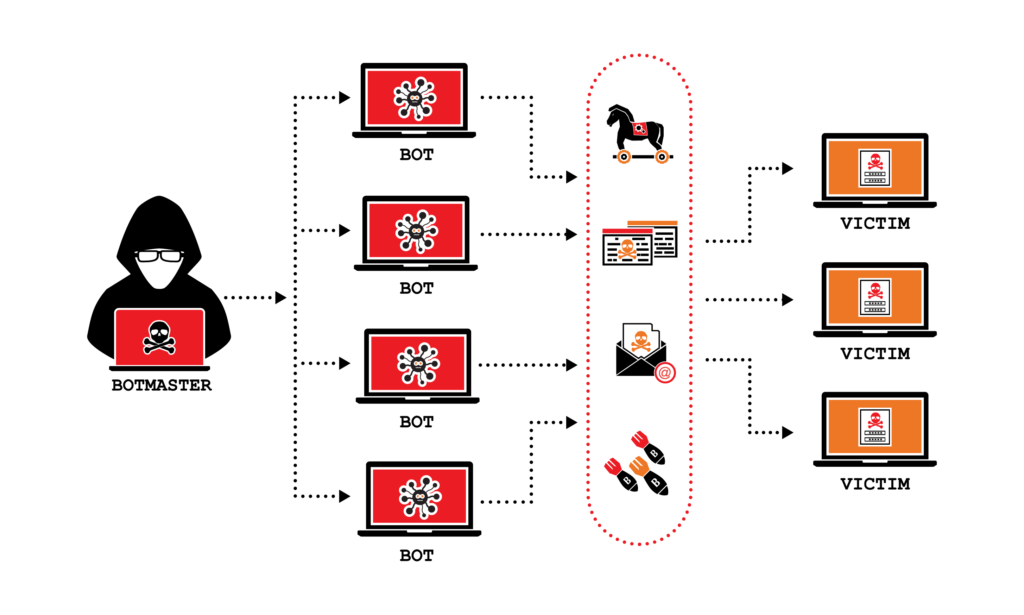
The Goal: Overwhelm and Shutdown
The main goal of a DDoS attack is to overwhelm the targeted online space until it becomes so slow or completely unavailable. Think of it like a highway during rush hour—too many cars trying to use the road at the same time, causing a traffic jam. For a website or service, this could mean it becomes incredibly slow for regular users or, in extreme cases, it might even crash.
Why Do People Do This?
The motives behind DDoS attacks can vary. Sometimes it’s about causing chaos or disruption just for the thrill of it, like a digital prank. Other times, it’s more malicious, such as aiming to bring down a competitor’s website or demanding money in exchange for stopping the attack. However, research suggests that the main reasons behind DDos are:
- Financial gain. The hacker may be seeking to hold a company at ransom – demanding that they pay money to stop the attack.
- Diversion. Another reason is to distract a company’s cyber defenses so that the hacker can try to infiltrate the company in another fashion.
- Competitive Advantage: Unscrupulous competitors might resort to DDoS attacks to gain an edge by undermining a rival’s online presence.
- Extortion: Cybercriminals may demand ransom to cease a DDoS attack, threatening to continue the assault unless a payment is made.
- Hacktivism. The hacker could be doing it to protest actions on the part of a company or government .
The DDoS Symphony: How Does it Play Out?
- The Gathering Storm (Preparation): Before the storm hits, cybercriminals assemble their botnet, a network of compromised computers, smart devices, and servers. These unsuspecting devices become unwitting soldiers in the impending DDoS onslaught.
- The Surge (Attack Phase): Once the botnet is ready, the attackers unleash a torrent of traffic toward the target. This surge in data, often in the form of requests or connection attempts, overwhelms the target’s infrastructure, causing it to buckle under the pressure.
- The Aftermath (Impact): As the target struggles to distinguish legitimate requests from the deluge of malicious traffic, services become sluggish or entirely unavailable. For businesses relying on online operations, the impact can be catastrophic, leading to financial losses, reputational damage, and customer frustration.
Types of DDoS Attacks
Our simplified definition of what DDoS is left out one detail: there are many different types of DDoS attacks that attackers can use depending on what specific server resource they’re trying to overload. Since we’re trying to keep things simple, we’ll just briefly highlight the broad types of DDoS attacks commonly used.
As mentioned previously, DDoS attacks are designed to jam up a website, usually by overloading a specific aspect of the site. For example, an attack could target the following to overload them:
- Web server resources such as CPU or RAM
- Database servers
- Network bandwidth
- DNS servers
- Etc.
Defending Against the Digital Traffic Tsunami
To defend against a DDoS attack, online spaces use various strategies. Imagine having a bouncer at the entrance of your party who checks each guest to make sure they’re real and not causing trouble. Online, there are tools and technologies that do something similar—filtering out the bad traffic and letting in the legitimate requests.
Read about our article on preventing this type of attacks including phishing, DLL hijacking and practicing clean cyber hygiene.
Conclusion
In a nutshell, a DDoS attack is like a digital traffic tsunami—too much for a website or online service to handle. Defending against it involves creating a strong digital bouncer to manage the crowd and ensure a smooth online experience for everyone. Understanding the anatomy of DDoS attacks empowers us to navigate the digital seas with resilience. By implementing proactive defenses and staying vigilant, we can weather the storms orchestrated by cybercriminals. Remember, in this ever-evolving digital landscape, knowledge is our most potent shield. Stay informed, stay secure, and together, we can brave the challenges of the online realm. Happy navigating!





