In this article, we provide insights into emerging trends in DDoS attacks and how businesses can adapt their cybersecurity strategies to stay ahead of the curve. DDoS attacks are on the rise, but hackers are also adapting their strategies to counteract growing mitigation techniques.
Of the many types of cyber threats, few are more frustrating and difficult to prevent than distributed denial-of-service (DDoS) attacks. These attacks can bring down even the largest websites by overloading servers with more requests than they can handle. Unable to meet the demand of junk requests, servers crash and often require hours to restore.
Norton, in fact, calls DDoS attacks “one of the most powerful weapons on the internet”, and with good reason. Denial-of-service attacks can come at any time, impact any part of a website’s operations or resources, and lead to massive amounts of service interruptions and huge financial losses. DDoS attacks were once a thing of mischief, but data shows they’re increasingly becoming a way for cybercriminals to make money or cause disruption for purposes.
Various DDoS attack types on the rise
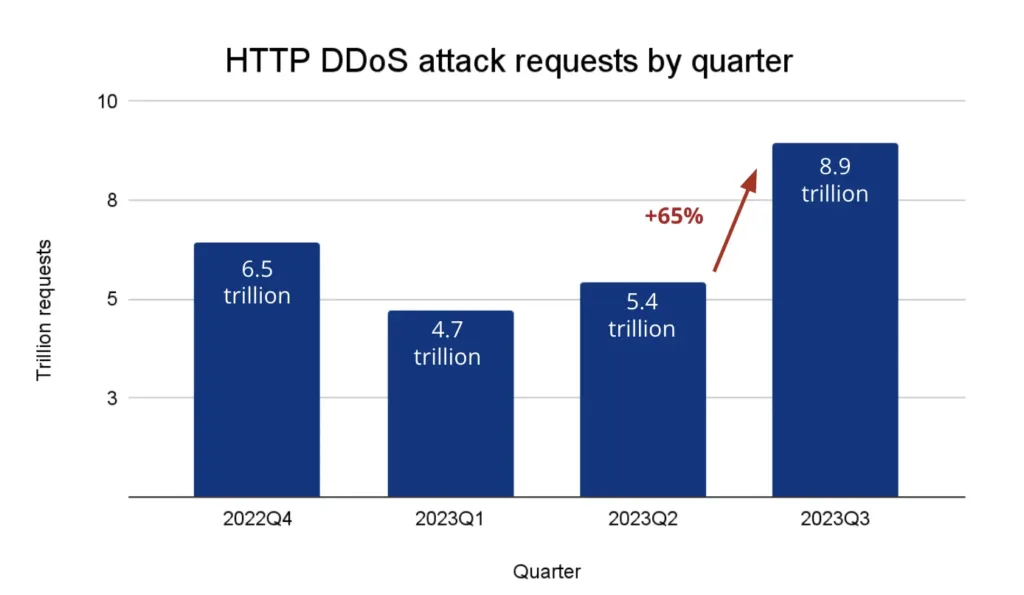
According to Cloudflare, in Q3 of 2022 the following trends in DDoS was observed:
- Ransom DDoS attacks increased by 67 percent year-on-year and 24 percent quarter-on-quarter.
- Online industries received the most application-layer DDoS attacks, recording a 131 percent increase quarter-on-quarter (and 300 percent year on year) rise in the number of attacks.
- Gaming and gambling companies were the most targeted by network-layer attacks, with a huge 405 percent increase in Mirai botnet attacks from Q2 to Q3 2022.
Trends in DDoS Attacks: A Dynamic Landscape
DDoS attacks have undergone a metamorphosis, evolving in sophistication and scale. As we embark on this journey into the future, understanding the emerging trends in DDoS is paramount for fortifying our digital defenses.
1. The Surge of IoT Botnets: A Growing Menace
The Internet of Things (IoT) has become an integral part of our connected world, but with its rise comes a new frontier for cyber adversaries. The surge of IoT botnets, witnessed in recent years, continues to be a growing menace. Hackers leverage insecure IoT devices to amplify DDoS attacks, creating formidable digital armies.
What to Watch For: IoT Security Posture
To navigate this trend, vigilant monitoring of IoT devices and bolstering their security posture are imperative. Organizations must ensure that IoT devices are not unwittingly transformed into tools of cyber warfare.
2. Artificial Intelligence (AI) in DDoS Attacks: The Rise of Smart Attacks
As AI technologies advance, cybercriminals are harnessing the power of machine learning to orchestrate more intelligent and adaptive DDoS attacks. Smart attacks, capable of learning and adapting to defenses in real-time, pose a significant threat.
What to Watch For: AI-Augmented Defenses
To counter the rise of AI-driven attacks, cybersecurity measures must evolve. AI-augmented defenses that can swiftly adapt to changing attack patterns will be crucial in staying one step ahead of intelligent adversaries.
3. Ransom DDoS (RDDoS): Extortion in the Digital Realm
The landscape of DDoS attacks is witnessing a shift towards extortion tactics. Ransom DDoS (RDDoS) attacks involve threat actors demanding payment to cease a sustained DDoS onslaught. This trend adds a new layer of complexity, turning DDoS into a business threat.
What to Watch For: Integrated Incident Response Plans
Facing RDDoS attacks requires organizations to have robust incident response plans that integrate technical defenses with a strategic approach to dealing with extortion attempts. Proactive communication and negotiation strategies become essential tools in navigating this emerging trend.
4. 5G Networks: A Double-Edged Sword in DDoS Defense
The rollout of 5G networks brings unprecedented speed and connectivity. However, the faster lanes also provide cyber attackers with a broader surface area to launch DDoS attacks. The increased bandwidth may facilitate larger-scale attacks with greater impact.
What to Watch For: Adaptive Network Security
The adoption of 5G demands a reevaluation of network security strategies. Adaptive network security measures, capable of dynamically responding to fluctuating traffic patterns and identifying anomalies, will be crucial in securing the accelerated digital highways.
5. DDoS Attacks as a Distraction: A Tactical Shift
In the chessboard of cyber warfare, DDoS attacks are increasingly being used as smokescreens to distract security teams from more insidious activities. While defenders focus on mitigating a DDoS onslaught, attackers may exploit vulnerabilities or execute more covert intrusions.
What to Watch For: Holistic Security Posture
To counter this tactical shift, organizations must adopt a holistic security posture. Beyond DDoS mitigation, the emphasis should be on comprehensive cybersecurity measures, including threat detection, vulnerability management, and incident response.
6. Quantum Computing: A Potential Game Changer
The prospect of quantum computing introduces a wildcard into the DDoS landscape. Quantum computers, when realized, could potentially break existing cryptographic algorithms, rendering current encryption methods obsolete. This could have profound implications for DDoS defenses.
What to Watch For: Quantum-Resistant Encryption
Preparing for the quantum era requires the adoption of quantum-resistant encryption methods. As the quantum threat looms on the horizon, organizations must future-proof their cryptographic protocols.
Top attacked industries by region
Now let’s dive deeper to understand trends in DDoS and which industries were targeted the most in each region.
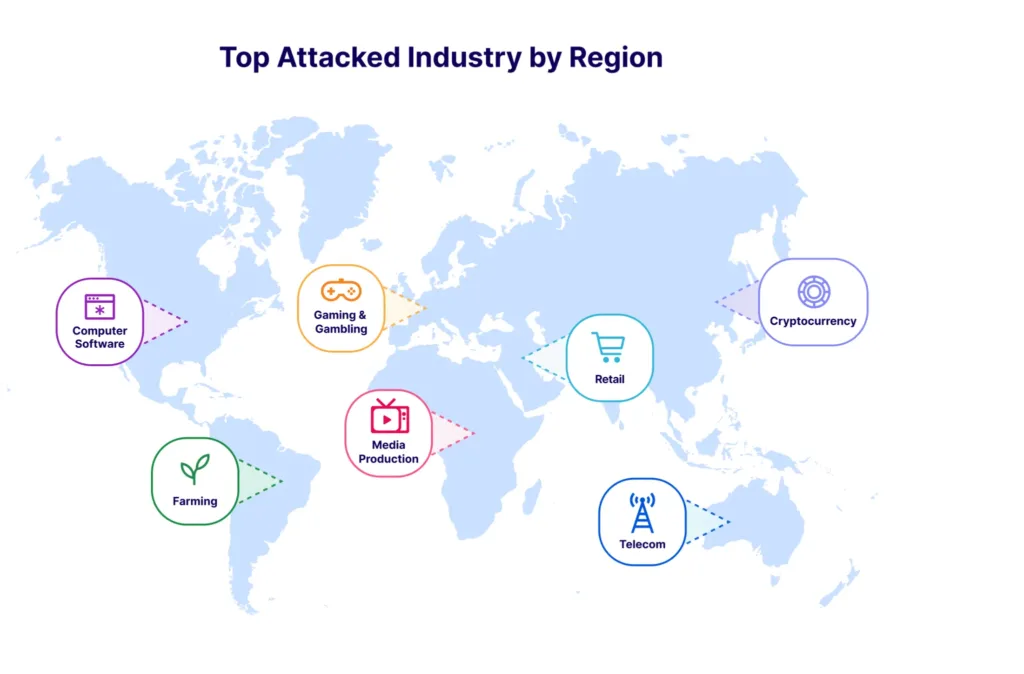
Africa: In Africa, trends in DDoS attacks frequently target telecommunications and financial sectors. With the increasing digitalization of financial services, cybercriminals exploit vulnerabilities to disrupt online transactions and gain unauthorized access.
Europe: In Europe, critical infrastructure industries, including energy and healthcare, bear the brunt of DDoS attacks. Threat actors aim to destabilize essential services, causing widespread impact and potential harm to public safety.
North America: North America sees DDoS attacks predominantly impacting farming, e-commerce and technology sectors. As major global tech hubs reside in this region, cyber adversaries exploit these connections, aiming to disrupt online platforms and compromise sensitive data.
Australia: Australia experiences frequent DDoS attacks against telecommunications, government entities and educational institutions. Cyber attackers target these sectors to disrupt services, compromise sensitive information, and potentially undermine national security.
Conclusion: Charting the Course Ahead
As we navigate the dynamic currents of emerging trends in DDoS attacks, one thing is certain—the landscape of digital warfare is ever-changing. The key to resilience lies in adaptability, vigilance, and a proactive approach to cybersecurity. By staying informed about these emerging trends in DDoS and preparing for the challenges they pose, we can fortify our digital ships and navigate the stormy seas of the cyber world with confidence.
In the grand tapestry of cybersecurity, each trends in DDoS is a thread that weaves into the larger narrative of digital defense. As guardians of the digital realm, let us embark on this journey together, ready to face the challenges and innovations that lie ahead. The horizon is vast, and the winds of change are blowing. Anchors aweigh, fellow cyber sailors—onward into the future we go!
DDoS terminology
Now that we have looked into trends in DDoS, let’s dig through DDoS facts might require brushing up on a few key terms. Distributed denial-of-service attacks are highly technical, and you may encounter some unfamiliar terminology while reviewing the latest stats.
- Denial-of-service attack: An attack on a website that sends an overload of traffic (requests) to a web server. A distributed denial of service attack (DDoS) uses multiple compromised computer systems to increase the number of requests that can be made to a server at one time, making server overloads easier to accomplish and more difficult to prevent.
- Amplification: A term used to describe a DDoS attack where the number of requests made to a target’s server is multiplied beyond the original request. There are several ways attackers can do this, including DNS amplification, UDP amplification, and ICMP amplification (Smurf Attack).
- Botnet: A network of computers infected and remotely controlled through a virus or malware program, that is used to make the requests to servers in a DDoS attack.
- Memcached: A distributed memory caching system popularly used in DDoS attacks.
- Mirai: Malware created to target Linux-based IoT devices, including home security cameras and routers. Mirai and its many variants are currently among the most-used malware to create DDoS botnets.
- Gigabytes-per-second and Terabytes-per-second: A measurement of how much data is sent to servers in a DDoS attack, typically denotated as GB/s or TB/s.
- Saturation: A term used for the amount of volume sent to a server during a DDoS attack. Supersaturation occurs when all of a system’s resources are filled with requests from the DDoS attack, completely shutting down the system, while sub-saturation refers to small DDoS attacks that can negatively impact system performance and resources but are not nearly large enough to shut down a server completely. Sub-saturating attacks are increasingly common, often go undetected, and are commonly used as a “smokescreen” for larger attacks.





