Emotet is a type of dangerous computer virus that spreads through email. It is designed to trick people into opening infected email attachments or clicking on malicious links. Once a computer is infected, Emotet can steal sensitive information, infect other computers, and cause serious harm to individuals and businesses. It’s essential to be cautious with emails and avoid clicking on unknown or suspicious links to protect against Emotet and similar threats.
Emotet Timeline
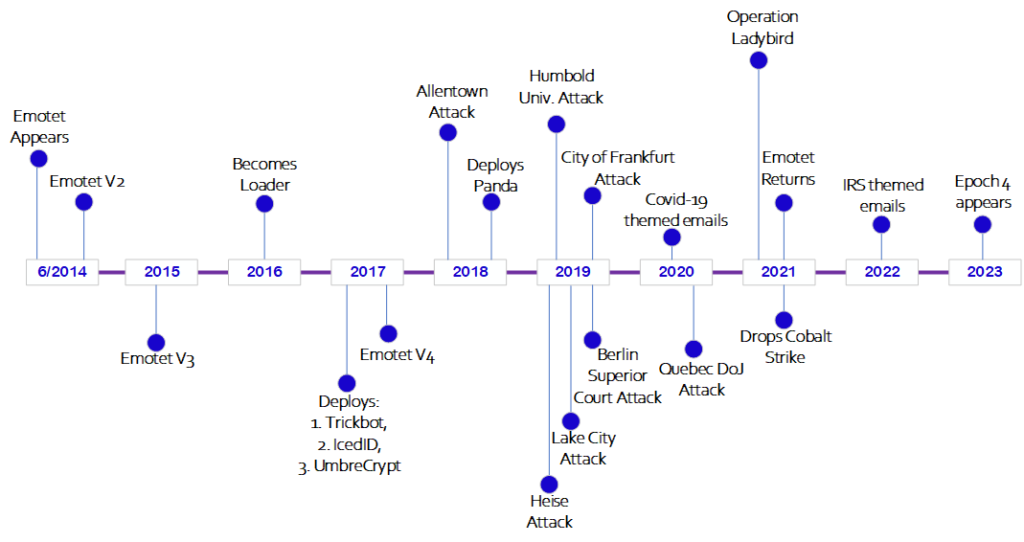
Emotet appeared in June 2014 under the name of Heodo/Geodo, and received its first major update (v2) at the end of the same year. These versions were generally aiming at Central European countries with developed economies – in particular Germany, Switzerland and Austria, so-called DACH. Key activity was circulating around banking data stealing. Through the following 1.5 years the activity of a newcomer was not noteworthy, although malware received another update (v3) and the ability to act as malware loader – the thing that became definitive for the future of Emotet.
How Emotet works
Here’s a detailed explanation of how Emotet works:
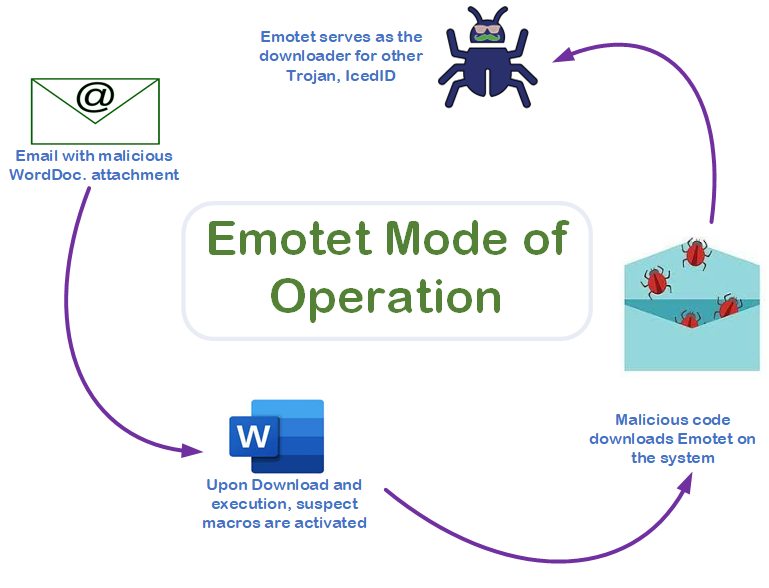
1. Infection Vector: Emotet’s main method of propagation is through malicious email attachments or links. The malware is commonly distributed via phishing emails that appear to be from legitimate sources, such as banks, government agencies, or well-known companies. These emails often use social engineering tactics to trick recipients into opening them.
2. Phishing Emails: The phishing emails used to distribute Emotet may contain compelling subject lines and body content designed to lure victims into acting. They often exploit fear, urgency, curiosity, or other emotions to entice recipients to open the email or click on links.
3. Malicious Attachments and Links: The phishing emails typically contain either malicious attachments (e.g., Word documents, PDFs, or Excel spreadsheets) or links to malicious websites. These attachments and links may seem harmless, but they carry hidden malicious payloads.
4. Macro-Based Infection: If a victim opens the malicious attachment, they are prompted to enable macros (small scripts) to view the document’s content. Once the macros are enabled, the Emotet payload is executed, and the infection process begins. Note that enabling macros in documents from untrusted sources is a dangerous practice and should be avoided.
5. Payload Delivery: Emotet’s payload is delivered and executed on the victim’s system. The malware is capable of spreading rapidly across a network, infecting other connected devices, including other computers, servers, and shared network resources.
6. Spreading and Persistence: Once inside a system, Emotet takes advantage of various techniques to remain persistent and evade detection by security software. It can inject its code into legitimate processes, create autorun entries, and modify system files to ensure it launches whenever the system starts.
7. Credential Theft: Emotet is designed to steal sensitive information, primarily login credentials, and financial data. It uses keylogging and form-grabbing techniques to capture usernames, passwords, credit card details, and other sensitive information entered by users on infected machines.
8. Botnet Formation: Emotet-infected machines form a botnet, a network of compromised devices under the control of a command-and-control (C2) server. The operators of Emotet can issue commands remotely to these infected devices, making the malware highly adaptable and capable of performing various malicious activities.
9. Payload Updates: Emotet is a modular malware, meaning it can download and install additional modules, or even different malware, on infected devices based on the attackers’ objectives. This allows the threat actors behind Emotet to use it as a gateway for deploying other malware strains like ransomware or banking Trojans.
How can businesses protect against Emotet?
Below are 13 techniques businesses can use to protect against Emotet
- Employee Education and Training: Conduct regular cybersecurity awareness training for all employees to help them recognize phishing emails, suspicious links, and malicious attachments. Make sure employees understand the potential consequences of falling victim to such attacks.
- Multi-Factor Authentication (MFA): Require MFA for accessing critical systems and sensitive information. This helps prevent unauthorized access, even if credentials are compromised.
- Regular Software Updates and Patching: Keep all software and operating systems up to date to close known vulnerabilities that attackers could exploit.
- Network Segmentation: Segment your network to limit the potential impact of a successful attack. This way, even if one part of the network is compromised, the entire infrastructure is not immediately accessible to the attackers.
- Robust Endpoint Protection: Deploy advanced endpoint protection software to detect and block malicious activities on users’ devices.
- Behavior-Based Detection: Use security tools that can analyze user and system behavior to detect anomalies and suspicious activities indicative of malware or unauthorized access.
- Incident Response Plan: Develop a comprehensive incident response plan that outlines specific steps to take in case of a security breach. Regularly test the plan through simulated exercises to ensure preparedness.
- Data Backup and Recovery: Regularly back up critical data and store it securely offline or in isolated networks. In case of a ransomware attack, having secure backups can help avoid paying ransom and restore systems faster.
- Penetration Testing and Security Audits: Conduct regular penetration testing and security audits to identify potential weaknesses and vulnerabilities in your infrastructure and applications.
- Vendor Management: Vet and monitor third-party vendors that have access to your systems and data, as they could be potential entry points for attackers.
- Restrict Macro Use: Disable macros in office productivity applications by default and enable them only for specific, authorized use cases.
- Email Authentication Protocols: Implement email authentication protocols like DMARC (Domain-based Message Authentication, Reporting, and Conformance), SPF (Sender Policy Framework), and DKIM (DomainKeys Identified Mail) to prevent email spoofing and impersonation.
- Strong Email Filtering: Implement robust email filtering solutions to block spam, phishing attempts, and known malicious attachments before they reach users’ inboxes. Consider using solutions that utilize machine learning and advanced threat intelligence to detect and prevent new, evolving threats.
Conclusion
Emotet’s modular and constantly evolving nature makes it challenging to combat. Its operators have been known to go dormant for periods and then resurface with new campaigns, which can catch organizations off guard. Engaging with cybersecurity experts and following industry best practices will help businesses stay ahead of potential threats. Defending against Emotet requires a combination of robust email security measures, employee education, regular software updates, endpoint protection, and proactive monitoring for signs of infection.





