In the rapidly evolving landscape of cyberspace, one malicious phenomenon has risen to prominence, leaving a trail of disruption and financial turmoil in its wake: ransomware attacks. These insidious threats have become more than just a headline; they’ve become a pervasive and evolving challenge that demands our attention. In this exploration, we embark on a journey to understand the rise of ransomware attacks from a human perspective – demystifying the motives, unraveling the methods, and contemplating the impact on individuals and organizations alike.
The Genesis of Ransomware Attacks
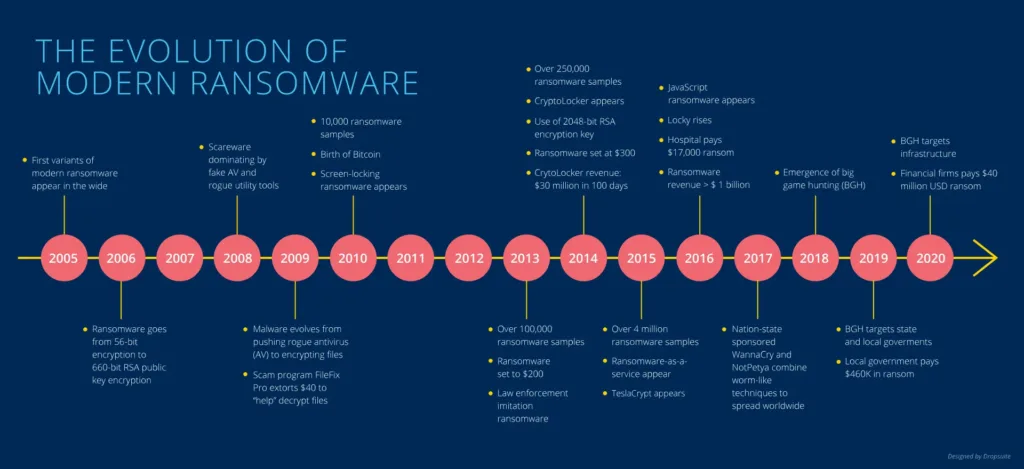
To truly comprehend the rise of ransomware, we must delve into its origins. Initially, ransomware was a covert tool deployed by cybercriminals to encrypt files on a victim’s computer, demanding a ransom – usually in cryptocurrency – for the release of the data. The anonymity afforded by cryptocurrency transactions proved to be a game-changer, fueling the proliferation of these attacks.
The genesis of ransomware attacks can be traced to the late 20th century when the first instances emerged as relatively simplistic tools. The concept of ransomware, however, crystallized in the mid-2000s with the advent of encryption-based attacks that held victims’ data hostage. The utilization of asymmetric encryption, coupled with the anonymity provided by cryptocurrency transactions, marked a significant shift in tactics. Cybercriminals recognized the potential for quick and untraceable financial gains. The ransomware landscape further evolved with the introduction of ransomware-as-a-service (RaaS), turning these attacks into a commodified criminal enterprise.
Over time, motives expanded beyond mere financial extortion to include political leverage, economic disruption, and ideological expression, painting a complex picture of ransomware’s evolution from rudimentary tools to a pervasive and multifaceted cyber threat.
The Evolution of Motives
As we navigate the landscape of ransomware attacks, it becomes apparent that motives have evolved beyond mere financial gain. While the lure of quick, untraceable profits remains a primary driver, cybercriminals have diversified their objectives. Today, ransomware is wielded as a tool for political leverage, economic disruption, and even ideological expression. The motives are as varied as the attackers themselves, painting a complex portrait of the modern cyber threat landscape.
The Human Impact
Behind the screens and lines of code, it’s crucial to acknowledge the profound human impact of ransomware attacks. Victims face not only financial losses but also emotional distress and a breach of privacy. Small businesses, often the target of choice, grapple with the existential threat of losing sensitive data or facing prolonged downtime. The human toll extends to the cybersecurity professionals tasked with mitigating these attacks, working tirelessly to safeguard digital spaces.
Ransomware attacks have a profound and often devastating impact on individuals, businesses, and communities, extending far beyond the realm of digital systems and financial losses. The human impact of ransomware attacks is multifaceted, encompassing emotional distress, privacy breaches, and the erosion of trust in digital spaces.
- Emotional Distress and Psychological Impact: Victims of ransomware attacks experience heightened levels of stress, anxiety, and frustration. The violation of personal or business data, often integral to one’s identity or livelihood, can lead to a sense of powerlessness and vulnerability. The emotional toll extends to feelings of anger, fear, and a loss of control over one’s digital life.
- Privacy Invasion and Breach of Trust: Ransomware attacks represent a violation of privacy as cybercriminals gain unauthorized access to personal and sensitive information. The breach of trust is profound, especially when individuals or organizations entrusted their data to digital platforms. The sense of violation is magnified when attackers threaten to expose confidential information, creating a lasting impact on the victim’s perception of digital security.
- Financial and Operational Consequences: For businesses, the financial consequences of ransomware attacks can be severe. Beyond the ransom payments, which are often discouraged due to the lack of guarantee for data recovery, there are costs associated with downtime, recovery efforts, and potential legal repercussions. Small businesses, in particular, may struggle to recover, facing the risk of closure and job losses, further amplifying the human impact.
- Impact on Cybersecurity Professionals: Cybersecurity professionals tasked with mitigating ransomware attacks face their own set of challenges. The pressure to safeguard digital spaces and recover compromised systems can lead to burnout. The constant battle against evolving cyber threats, coupled with the emotional weight of protecting individuals and organizations, underscores the toll on the mental health and well-being of these professionals.
- Community and Societal Trust: Ransomware attacks erode trust not only at the individual level but also within communities and society at large. As these attacks become more prevalent, there’s a growing sense of insecurity and mistrust in digital platforms and services. The fear of falling victim to ransomware can alter behaviors, affecting how individuals and businesses engage with digital technologies.
In essence, the human impact of ransomware attacks extends well beyond the immediate financial losses. It permeates the emotional, psychological, and societal fabric, emphasizing the urgent need for comprehensive cybersecurity measures and a collective effort to protect against these increasingly sophisticated threats.
Tactics and Techniques
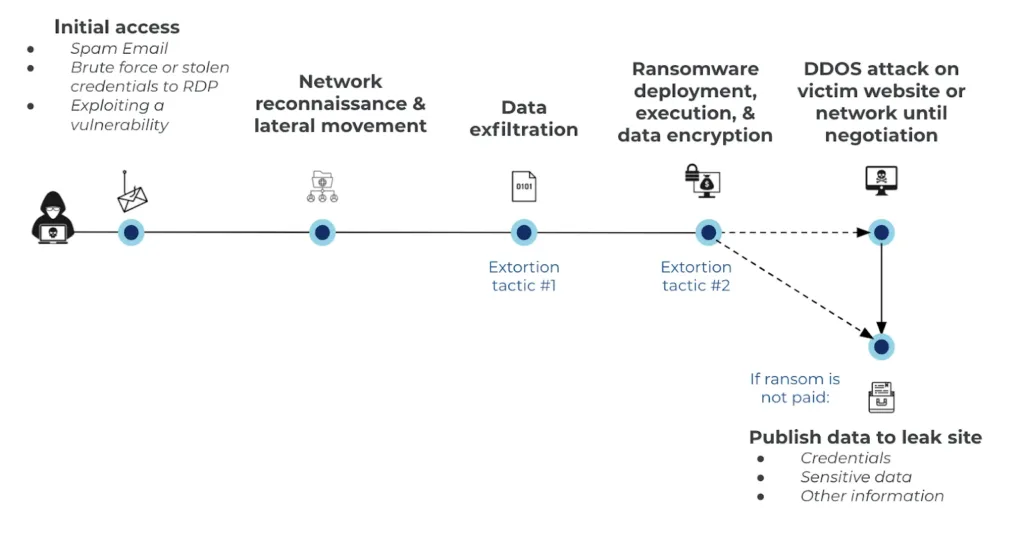
Understanding the rise of ransomware demands a closer look at the tactics and techniques employed by cybercriminals. Spear-phishing, exploiting software vulnerabilities, and utilizing malicious attachments are just a few entry points. Ransomware-as-a-Service (RaaS) platforms have democratized access to these tools, allowing even less technically adept individuals to launch attacks.
The commodification of ransomware has democratized the threat landscape, making it more accessible to a broader range of malicious actors. Ransomware tactics are a multifaceted arsenal employed by cybercriminals to infiltrate systems, encrypt data, and extort victims for financial gain. Understanding these tactics is crucial for individuals and organizations seeking to fortify their defenses against these insidious threats.
- Phishing and Social Engineering: One of the most prevalent tactics is phishing, where cybercriminals use deceptive emails, messages, or malicious websites to trick individuals into clicking on malicious links or downloading infected attachments. Social engineering plays a pivotal role, exploiting human vulnerabilities by masquerading as trusted entities or manipulating emotions to elicit actions that compromise security.
- Exploiting Software Vulnerabilities: Cybercriminals often exploit weaknesses in software or operating systems to gain unauthorized access. This tactic involves identifying and targeting vulnerabilities in outdated or unpatched software, allowing attackers to infiltrate systems and deploy ransomware. Regular software updates and patch management are crucial defenses against this tactic.
- Ransomware-as-a-Service (RaaS): Ransomware-as-a-Service is a model where cybercriminals, sometimes operating as part of larger criminal organizations, offer ransomware toolkits to less technically proficient individuals. This commodification of ransomware allows a broader range of actors to launch attacks. RaaS platforms often provide a user-friendly interface, customer support, and profit-sharing models, democratizing access to ransomware tools.
- Double Extortion: A more recent and potent tactic is double extortion, where cybercriminals not only encrypt the victim’s data but also exfiltrate sensitive information. The threat of exposing this data adds an extra layer of pressure, compelling victims to pay the ransom to prevent the public release of confidential information. This tactic increases the stakes for victims and exacerbates the impact of ransomware attacks.
In essence, ransomware tactics are continually evolving, driven by a combination of technological advancements, criminal ingenuity, and the potential for lucrative financial gains. A holistic defense strategy involves cybersecurity measures, regular updates, user education, and a proactive approach to mitigate the risks posed by these tactics.
The Business of Ransom:
As ransomware attacks burgeon, the economics behind them have become increasingly sophisticated. Ransomware cartels and syndicates operate with a level of organization reminiscent of legitimate businesses. Negotiations for ransom payments, customer support, and even user interfaces mimicking customer service portals are now commonplace. This professionalization underscores the gravity of the threat and challenges the traditional view of cybercriminals as lone actors.
Combating the Rise:
Combatting the rise of ransomware attacks requires a multifaceted approach that integrates technological defenses, user education, and proactive cybersecurity measures. Here are key strategies to mitigate the threat of ransomware:
Regular Data Backups: Implement a robust backup strategy to regularly back up critical data. Ensure backups are stored in an isolated environment and routinely tested for reliability. In the event of a ransomware attack, having up-to-date backups can facilitate data recovery without succumbing to extortion.
User Education and Awareness: Educate users about the risks of phishing emails, malicious attachments, and suspicious links. Promote a culture of cybersecurity awareness within organizations to empower individuals to recognize and report potential threats. Regular training sessions and simulated phishing exercises can enhance user vigilance.
Update and Patch Systems: Regularly update and patch software, operating systems, and applications to address known vulnerabilities. Cybercriminals often exploit outdated software to infiltrate systems. Automated patch management systems can streamline the process of keeping systems up to date.
Implement Security Software: Utilize comprehensive cybersecurity software that includes antivirus, anti-malware, and intrusion detection systems. Endpoint protection solutions can help detect and mitigate ransomware threats before they can cause significant harm.
Network Segmentation: Segmenting networks can limit the lateral movement of ransomware within an organization. If one segment is compromised, it reduces the risk of the entire network being affected. This containment strategy is an effective way to minimize the impact of an attack.
Ransomware Response Plan: Develop and regularly test a ransomware response plan that outlines clear steps to take in the event of an attack. This plan should include communication protocols, contact information for law enforcement and cybersecurity experts, and a decision-making framework for responding to extortion demands.
Zero Trust Security Model: Adopt a Zero Trust security model, where trust is never assumed, and verification is required from everyone trying to access resources. This model helps prevent lateral movement and restricts access privileges, reducing the attack surface for ransomware.
Collaborate with Law Enforcement: Collaborate with law enforcement agencies to report incidents and gather intelligence on emerging threats. Engaging with cybersecurity communities and information-sharing platforms can enhance collective efforts to combat ransomware.
Encourage Responsible Use of Cryptocurrencies: Cryptocurrencies are often the preferred method for ransom payments. Encourage responsible use by working with cryptocurrency exchanges, financial institutions, and law enforcement to trace and block ransom transactions.
Incident Response and Recovery: Establish a comprehensive incident response plan that includes not only immediate actions during an attack but also strategies for recovery and system restoration. Engage with cybersecurity experts who specialize in ransomware mitigation.
Legislation and Regulation: Advocate for and comply with cybersecurity regulations that promote a proactive and secure environment. Legislation can incentivize organizations to invest in cybersecurity measures and deter cybercriminals.
Combating the rise of ransomware requires a holistic and collaborative effort, involving individuals, organizations, and government agencies. By combining technological defenses with user education and strategic planning, the collective resilience against ransomware attacks can be significantly strengthened.
The Future Landscape:
As we peer into the future, it’s clear that ransomware attacks will continue to adapt and evolve. The intersection of artificial intelligence, cryptocurrency, and an ever-connected world presents both challenges and opportunities. Cybersecurity professionals, policymakers, and individuals alike must collaborate to stay ahead of the curve, fostering a collective defense against the evolving threat landscape.
In conclusion, understanding the rise of ransomware attacks is not merely an exercise in cybersecurity awareness; it’s a call to action. By recognizing the human impact, motives, tactics, and future trends, we equip ourselves to navigate the digital realm with vigilance and resilience. The fight against ransomware is a shared responsibility, demanding our collective commitment to securing the interconnected tapestry of the digital world.





